Table of Contents
- Intro
- The Goal
- The Google Pixel Tablet, from a hardware point of view
- Google, the National Security Agency, and Data Link-Ability
- Critical Notes
- Device Purchase Strategies
- Device Setup Directions
- DEFCON ONE configuration

Intro
This guide is aimed at providing a detailed method for maximizing security and privacy on a Google Pixel Tablet (2023). This guide should be adapted to fit your threat model. While this guide aims to provide a high level of operational security, I am not your security engineer. If you'd like to hire me to talk about your threat model, please see stellarwind.nl.
Legacy phone calling and texting (SMS, MMS) are inherently insecure. Communications content and metadata is collected and stored by various organizations and for many years. All people, but especially those in at-risk professions, have a responsibility to safeguard their communications with strong encryption technologies. Only then will your coworkers, friends, and family be able to collectively defend your rights. In professions where privacy is expected between you and clients like law and journalism, policy should dictate to either communicate securely or not at all.
Encryption technology is not new but default strong encryption in mass-market devices is. The political cost of default privacy and security is at an all-time low while the social expectations of strong encryption are at an all-time high. Modern telecommunications largely depend on legacy and vulnerable communications infrastructure, which is by design:
- All cell phones (baseband processor) transmit insecure content and metadata because cell networks were designed for connectivity and surveillance of said connectivity.
- All cell phones (baseband processor) not broken, off, or in Airplane Mode can be easily tracked.
- The majority of SIM cards require registration using government-issued ID.
- Most Androids get slowly patched, if at all.
- Carrier modified versions of Android are poorly developed and maintained.
“Nobody is listening to your telephone calls” –President Obama, 2013
President Obama is not lying. It is not possible for the US government to "listen" to every phone call. However, the technical requirements for recording phone calls (MYSTIC, DAPINO GAMMA) and text messages (DISHFIRE) is more than feasible. It is cheaper and more effective to transcribe voice data to text, transcriptions that can be stored forever. The solution is easy: don’t give it to them.
What is bad for U.S. Intelligence is also bad for all other malicious actors. It is up to us to cause the social change that in turn lowers the personal costs of default privacy and security and the financial risk of businesses to support what we need.
The financial cost of surveillance equipment is also at an all-time low. Mobile IMSI catchers can be built and deployed by anyone technically savvy enough to learn how to build one, and law enforcement has large budgets for more feature rich devices. The most effective way to assure that you are not a victim of cell tracking or attack is to not use those systems.
The Goal
The goal of this guide is to install CalyxOS (or GrapheneOS if you choose) onto a Google Pixel Tablet, which is not a cellular device (no baseband processor). Using CalyxOS streamlines the install and use of Orbot (Tor) and Signal while also not using Google services of any kind. At the end of this guide is an optional DEFCON ONE configuration that may further mitigate certain kinds of attackers.
The Google Pixel Tablet, from a hardware point of view
The Pixel Tablet fills a much needed space:
- Supports Wi-Fi only
- Supports Tensor SoC & Titan M2
- Supports CalyxOS or GrapheneOS
- Supports Signal via F-Droid
- Supports Orbot also via F-Droid
- Supports wired headsets for audio and video calls via USB-C
- Supports wired ethernet adapters via USB-C
Blending In
One reason why Tor is so valuable compared to any for-profit VPN provider is that you blend in with everyone else using Tor. Don't stick out. Using "un-hackable phones" or hardware-modded devices sticks out. Using commodity hardware like a Google Pixel device does not. This has important value for both physical surveillance and network surveillance.
Why not use a phone in Airplane Mode? Why does it need to be a Wi-Fi-only device?
In cell phones (devices with cellular baseband processors), the baseband is an isolated computer within the phone, with its own power controller, CPU, memory, firmware, and operating system. When a phone boots up, the initialization sequence of the phone includes the boot up of the baseband. This means that the baseband is initialized, before and in parallel to, the phone's main SoC and operating system. This is done for power-saving and security reasons. It means that when you put a phone into Airplane Mode, all you're doing is turning your phone's operating system's access to the baseband off. Airplane Mode does not guarantee that the baseband hardware, firmware, or software stack is turned off. Airplane Mode effectively preventing baseband from I/O'ing may be dependent on the hardware, firmware, and OS of the deivce, and it should be presumed that no baseband is trustworthy unless proven otherwise.
Another issue is that Airplane Mode is an OS feature. If the OS hasn't even booted, a user has extremely limited control over baseband. Recently confirming this issue is a security researcher observing an RF spike during cellular Pixel devices (phones, with basebands) during boot. Wether it's a hardware or firmware design decision, or accident, different operating systems cannot guarantee that lower levels of a phone will not behave in unexpected ways, particularly during the phone's boot process before the OS even initializes. It should be assumed that every kernel patch and every firmware patch may change the behavior of baseband. Testing all patch levels with RF meters would be necessary to guarantee expected outcomes. Or, don't use devices with basebands.
Even without a SIM card, with Airplane Mode not enabled, a baseband processor can and does connect to cell towers, including the disclosure of the device's IMEI along with "when" and "where" metadata (read more here). This is how a SIM-less phone can call 911. It's impossible to mitigate cellular communications without resorting to Faraday cages.
Google, the National Security Agency, and Data Link-Ability
Google is an American company that works with the NSA and is part of the PRISM program. If you are, or ever could be a target of U.S. intelligence or U.S. military organizations, you are already playing difficult game by choosing a Google product. However, you probably aren't defending against the NSA. Not all adversaries are the NSA, nor do they have the budgets and reach as the NSA. Risk minimization should not always be compared to NSA-style actors. Care about your threat model, not someone else's.
Just turning on a Google product with stock Android, the device is working against you by collecting WiFi and Bluetooth network information in order to attempt to "streamline" a user's setup experience. Some of that data is uploaded to Google's servers as soon as the device is connected to the internet. Every Google device, especially new ones, upload its unique hardware identifiers to Google, along with network metadata that can disclose physical location information to Google.
- Your mobile device's hardware identifiers, like a MAC address.
- Your wireless access point (WAP) MAC address and SSID.
- All of your neighbor's WAP's MACs and SSIDs.
- Your public IP address used to connect to *.google.com services.
- If your WAP, or any of your neighbor's WAPs observe your real MAC address, and those WAPs are cloud connected, it should be presumed that those WAPs will report the metadata associated with seeing your MAC at that location to a cloud database.
Note: CalyxOS, by default, uses MAC address randomization.
If Google, or any of the U.S. intelligence or military organizations, have any other data that links anything about you to the this Google device, your identity can be tracked by these organizations via data link-ability. Other secondary data points about this device can and will be linked to you if targeted:
- Your bank card used to make the purchase.
- Your physical address for device delivery, if bought online.
- Your car license plate seen by Automatic License Plate Readers (ALPR) going to pick up the device.
- Face survaillance systems as you travel to and from a physical store to buy the device.
Google Firebase Cloud Messaging (FCM)
When using Signal on a device running Android, such as a Google Pixel Tablet, it requires the use of Firebase Cloud Messaging (FCM). This indicates that Google has access to metadata records of when, where, and what service you're using. NSA/FVEY is spying on and storing this data.
Per Meredith Whittaker, Signal's President, "In Signal, push notifications simply act as a ping that tells the app to wake up. They don't reveal who sent the message or who is calling (not to Apple, Google, or anyone). Notifications are processed entirely on your device."
That "ping" is more than just a ping, and requires Google to have a lot of data about the target service and the target device. Google is able to see, and thus FVEY is able to make a permanent record of:
- FCM identifiers, such as hardware identifiers, of who is receiving a message.
- The messaging application; in this case, Signal.
- The date and time associated with received messages.
- Any network metadata, such as IP, associated with receiving messages.
All of this can and will be used with FVEY's other records, such as internet backbone or ISP metadata, and will be used to confirm assumptions made when identifying who is talking to whom.
To further break this down:
- A Signal user sends a message to an Android user via Signal (the receiver).
- Signal's servers notify FCM that there is a message or call waiting for a specific user.
- FCM "pings" the specific user's Android device.
- The receiver's Android device receives the "ping" and notifies the end user that there are new Signal messages, or a call.
- The receiver's Signal application then activates and requests any new messages (or calls) from Signal's servers.
After wiping stock Android off the Pixel Tablet, which the CalyxOS setup process does, a user is able to opt-in to installing Google services. This is how to evade FCM: by not installing Google services. CalyxOS is Android without any Google services by default, and Signal can be installed trivially and operate without FCM. Further, CalyxOS makes it trivial to install and use Orbot (Tor), system wide. Orbot significantly enhances network metadata surveillance resistance to a global passive adversary (GPA; in other words, someone who is able to surveil tremendous amounts of the internet).
Critical Notes
Wi-Fi tablet + Signal advantages
- The Pixel Tablet does not have a baseband processor, SIM card, or SIM card port insecurities.
- You can control which Wi-Fi networks to expose your device to, if you choose to use Wi-Fi.
- The Pixel Tablet employs default Full Disk Encryption that is dependent on hardware and firmware cryptographic integrity controls.
- CalyxOS publishes security patches quickly and are not dependent on carrier restrictions.
- Signal uses only modern, always-on, end-to-end cryptography. As of September 2023, Signal now has quantum resistance.
- Signal allows users to verify encryption key fingerprints.
- Signal is free, open source, and has public security audits.
- Signal supports interoperability, meaning that other people can use Signal on iOS or Android devices.
- CalyxOS employes good security and privacy protections by default. For example, a cloud account is not necessary to download, install, or update apps such as Signal (via F-Droid).
Wi-Fi tablet + Signal disadvantages
- Wired or Wi-Fi internet access is not as abundant as cellular internet access. These days, people depend heavily on having an always-connected device to function.
- Setting up CalyxOS on an Android device, while straight forward, will feel very daunting to a non-technical individual. Calyx Institute made its own installer to automate the process as much as possible, and it's a huge help.
Notes on Device Charging
Only use genuine Google chargers and charging cables that you have purchased yourself, ideally in-person with cash. Do not use friend's, family's, or borrow stranger's chargers or charging cables. Do not use third-party chargers or charging cables. Do not let anyone else use your chargers or charging cables. Read more here.
Please note that the Pixel Tablet does not come with a USB-C charger in the box. Because Google wants people to use this as a "connected home" device, there's a speaker stand that comes included with the tablet, and the charging cable is a proprietary barrel plug that is only for the speaker/charging stand.
Device Purchase Strategies
Again, this largely depends on your threat model.
In my case, for fun, I asked a friend to drive me to the store in their car. The benefits of this is that automatic license plate readers (ALPRs) will not observe me moving through public streets. I asked them to drive me to a different city, one that I've never spent any time in before, but one that has a Best Buy. I brought $550 USD to a Best Buy.
After the purchase, since we were already in a city that I'd spent no time in before, we went to a small cafe with free internet. Not a Starbucks. Starbucks has a huge global surveillance network of wireless access points that all centrally log devices and user activity. I unboxed the Pixel Tablet in my friend's car then used the cafe's wifi to connect to the internet for the setup process.
Device Setup Directions
- Powered on, clicked Get Started
- Set up offline then continue
- Set the time
- Disable location
- Disable diagnostic data
- Set a simple PIN
- Opt-out of setting up biometric authentication
- Settings > System > System Update
This is a necessary step in order to install the most up to date device firmware. My device had a March 2023 patch level (11 months old). The update on my Pixel Tablet took roughly 30 to 45 minutes.
- Reboot
- Settings > About Tablet > Tap “Build Number” 9 times to unlock Developer Mode
- Settings > System > Developer Options > Enable USB Debugging
- Settings > System > Developer Options > Enable OEM Unlocking
- Enable the tablet’s Airplane Mode
I then had my friend drive me home.
From a personal laptop, Go home, follow setup directions from calyxos.org
After CalyxOS is installed:
- Connect to WiFi (unless you have stalkers, read DEFCON ONE at the bottom of the guide first!)
- Disable Google Services Compatibility
- Uncheck all of the optional apps except for: OnionShare, Orbot, Signal, and Tor Browser for Android
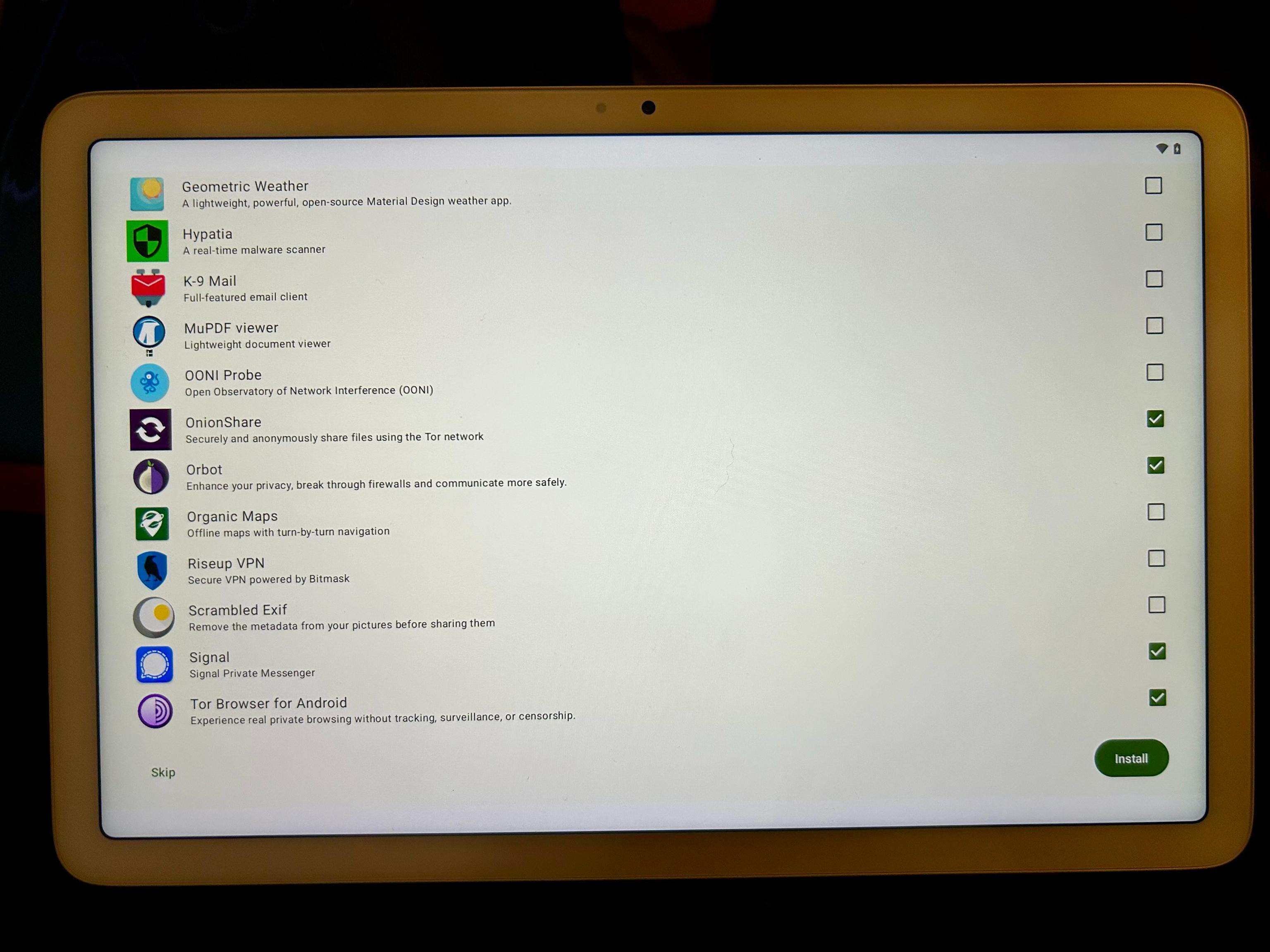
Click Install. All done!

I added a couple of shortcuts to the homescreen and changed the wallapaper to a different one preinstalled on the device, just for fun.
Setting up Orbot
First, to protect network metadata:
- Open up Orbot
- Click Connect
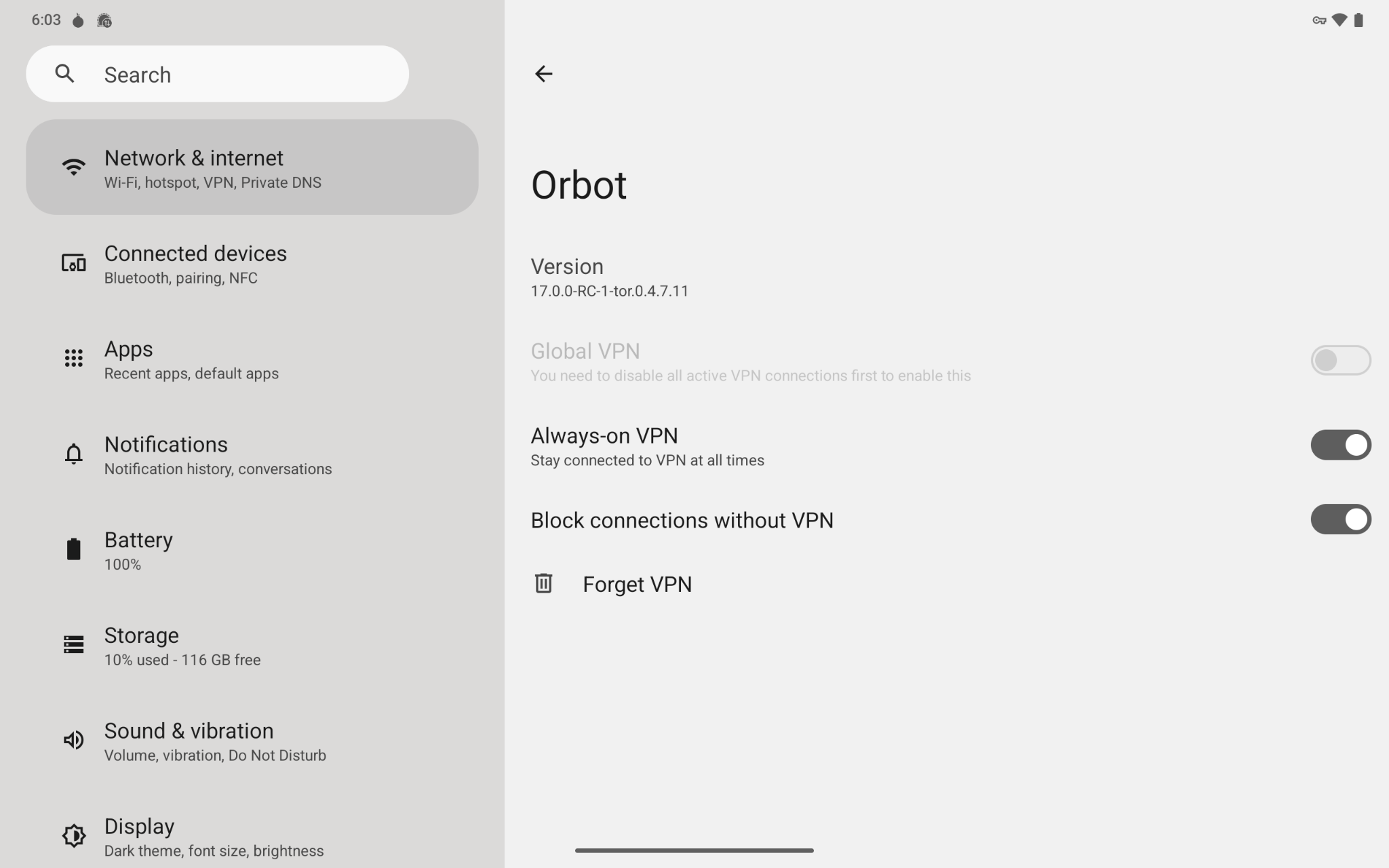
- Go to Settings > Network & Settings > VPN > Orbot (settings, on the right) > Enable Always-on VPN and Enable Block connections without VPN
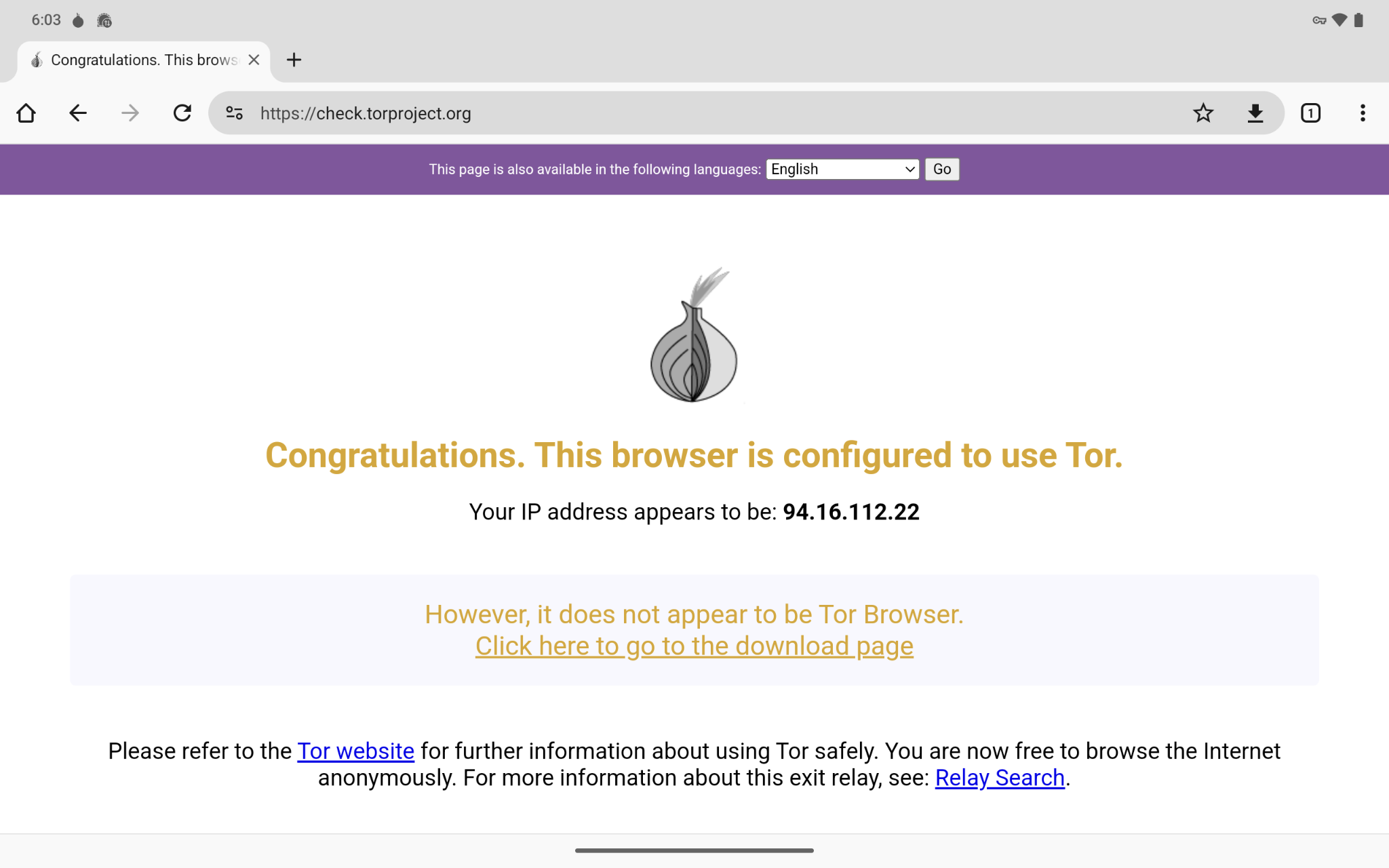
As a precaution, I used the pre-installed Chromium browser (not Tor Browser, intentionally) to check to see if Android (CalyxOS) is being torified by Orbot. I simply go to check.torproject.org.
Note, this tablet should not be used for any other web browsing unless Javascript is competely disabled.
Setting up Signal
There are lots of choicees to be made here. What's most important when choosing a Signal number is that you have long-term, secure control of the phone number, or trust the person or organization managing the phone number. Choosing the right method really depends on your threat model and your goals for your publicity or anonymity.
Journalists, lawyers, and other professionals might have an already-public phone number given to them from their employer. You can use that phone number in Signal on this device, and on this device only.
Americans can leverage Google Voice. Digital phone number serices might be a good solution for a Signal phone number, but only if access and control of that phone number is legitimately secure. Google Voice, for example, leverages the same nation-state defences that Gmail accounts use. Two-factor authentication must be used to access these services. Americans with access to Google Voice can also pay Google $20 to transfer in a phone number to Google Voice, and doing so will make it a permanent number on your Google account and will not get purged due to lack of activity.
You can request that a friend or family member add a new phone number to their cellular provider's plan. Activate the phone number on an old cell phone and get the Signal registration SMS, then destroy that phone and SIM card, and remember anchor points (dont activate the phone number and use cellular services in places where you regularly go).
Notes on the use of the Contacts, Calendars, and Notes apps
You have two choices when it comes to managing your contacts list, calendars, and notes data. There are many pros and cons with these two options and will depend on your threat model, so please think very carefully about your operational security practices.
Offline data: Since you can't sign into a Google account on this CalyxOS device, you cannot risk disclosing your contacts, calendars, and notes data to Google or your local government willingly (if your government has forced Google to host your data in your country instead of, or in addition to, the USA). This means it is relatively safe to use the on-device Contacts, Calendar, and Notes apps, depending on your threat model. Using CalyxOS's Contacts app is seamless since you can safely grant Signal access to contacts, if it asks.
- You have to trust Signal to continue to implement trustworthy cryptographic security mechanisms that continue to prevent themselves from ever having cleartext access to your contacts. This risk is low, since you are already trusting Signal with the confidentiality and integrity of the content of your communications and whom you communicate with via Signal. This risk is also low because Signal does not have any financial motivation to collect your contacts in any way. In fact, data storage is expensive, and responding to government requests for users data is expensive, so it is cheaper for Signal to never have this data.
- WIP
Android-native apps are the default places to look for this data if you ever are stopped and searched by government or private security agents. If this risk applies to you, store your data in a trustworthy offline password manager that supports a "key file" like Strongbox. Strongbox is like KeypassXC but for iOS, where the database is encrypted in addition to iOS disk encryption, but you can use a key file to make bruteforcing of this database impossible. Keep your key file online somewhere so you can remotely download it when you need access to your Strongbox database contents. Like your passphrase to the database, the key file should never be shared.
Online data: If you are technically savvy, or have access to trustworthy technical friends or coworkers, you can self host your contacts, calendars, and notes. I use Mail-in-a-Box to self host these things, but there are many open source, self-host solutions out there.
- Since data is remotely available, you can easily wipe your phone when crossing security check points, including regional borders like at airports, and re-setup your device and re-download your data from anywhere in the world after you have safely cross these types of high-risk areas.
- Since data is remotely available, it may be possible for your adversaries to know of the existence of where your data is stored online. In my example of using Mail-in-a-Box, this setup requires a public domain name that is registered to my name. Government and private entities can buy full access to domain registry data. Online storage is a risk for remote exploitation by way of illegal or legal (government warrant) means.
- Running your own Tor hidden service, like from a Raspberry Pi hosted in a secure location, means that you can use Tor Browser to safely and privately access or download remote data.
DEFCON ONE configuration
Why DEFCON ONE might be critical for you
Are you worried about, or have you ever experienced, attackers physically stalking, harassing, or assaulting you? If the answer is yes, then you have a high risk of those same abusers conducting wireless attacks against your wireless devices.
Wireless (Wi-Fi or Bluetooth) attacks are "physical" attacks since they have to physically capture the electromagnetic waves passing though the air near you. They may aim to:
- Capture your wireless packets in order to conduct surveillance. Your abusers might be trying to determine:
- Are you nearby?
- When are you online and active?
- How long are your conversations?
- How often do you have conversations?
- Capture your wireless packets in order to attempt to hack the security vulnerabilities in wireless protocols. Your abusers might be trying to determine:
- What type of device are you using?
- What methods are you using in order to communicate with others?
- Are there any vulnerabilities that could be taken advantage of?
- DoS (Denial of Service) your device to prevent you from being able to communicate.
- Hack the wireless protocols allowing active surveillance of wireless transmissions or to hack the device through protocol, driver, or operating system vulnerabilities. Your abusers might be trying to determine:
- What apps are you using?
- Do those apps have any vulnerabilities?
- Hack the wireless device directly through unknown or unpatched vulnerabilities in the wireless service, driver, and/or operating system. Your abusers might be trying to:
- Have complete access to your device, including apps like Signal.
DEFCON ONE setup directions
Perform these steps after installing CalyxOS, but booting CalysOS, and especially before enabling internet connectivity in CalyxOS.
- Use a network router at your home or office that allows the use of wired ethernet.
- Use a USB-C to gigabit ethernet adapter to connect the Pixel Tablet to the router via wired eithernet cable.
- Before booting CalyxOS (when you have not configured any wireless network) connect the ethernet adapter to the CalysOX-installed tablet.
CalyxOS should automatically default to the wired connection. However, wired success may depend on the ethernet adapter. When I tried this on my tablet, my Belkin adapter, which was made for Apple devices, did not work. I'll order one for Android and verify this works soon(TM).
Notes on DEFCON ONE configuration
- An ethernet adapter does not support USB-C charging. You will not be able to leave the tablet with an always-on internet connection, but that is not necessarily a bad thing. You might, instead, purchase an adapter that supports both wired ethernet and a USB-C power cable port.
- Assure that Airplane Mode is enabled immediately after setting up the tablet for the first time. Assure that Airplane Mode is always enabled, presuming wired ethernet will work in this configuration. Assure that you never connect to any Wi-Fi access point, ever, so that if Airplane Mode ever becomes disabled accidentally, it will not broadcast any Wi-Fi connect packets with a real MAC address.
yawnbox